If you are in the field of web application testing and security testing, then you must have heard of Burp Suite. It is a comprehensive and integrated platform for performing security testing of web applications. Burp Suite is developed by PortSwigger and is used by security professionals, penetration testers, and web developers worldwide.
With Burp Suite, you can perform various types of security testing, including web application scanning, vulnerability identification, and exploitation. The tool provides a wealth of features that make it easier to identify and exploit security vulnerabilities in web applications.
Interception Proxy
The Interception proxy allows you to intercept, inspect, and modify the requests and responses between your browser and the target application. You can use this feature to observe and manipulate the requests and responses in real time, allowing you to identify and test for vulnerabilities in the application.
Spider
Burp Suite’s Spider tool automates the process of crawling a web application to identify its accessible pages and functionality. Spidering is crucial for web app security testing and discovering hidden pages, input fields, and other functionality. To begin a spider scan, users can follow links within the application or use different techniques like parsing sitemaps or brute-forcing directories and file names to discover new URLs.
Scanner
Burp Suite users employ Scanner, a powerful automated vulnerability scanner tool, to identify and exploit web application vulnerabilities. Scanner sends many requests to the target application automatically and identifies/exploits common vulnerabilities such as SQL injection, XSS, CSRF, etc.
Intruder
In Burp Suite, users can automate web application parameter testing using Intruder. It tests input fields for SQL injection, XSS, and other vulnerabilities. Intruder is versatile and tests text fields, checkboxes, dropdown menus, and more. To use Intruder, select a target input field, customize a payload list, and configure the attack settings to include headers or cookies.
Repeater
Repeater is a powerful tool in Burp Suite that allows the user to manually manipulate and resend individual HTTP requests to the target application making it an essential tool for testing and debugging web applications. It is designed to provide the user with an easy way to modify and resend requests to the server to explore and verify the application’s behavior.
Sequencer
Burp Suite users apply the Sequencer tool to test the unpredictability of session tokens or other values that web applications produce. It checks the randomness of these values and how hard it would be for attackers to guess them. The Sequencer tool captures the target web app’s generated values, including session tokens or other tokens used to maintain state, and examines them to identify any exploitable patterns or biases or to check if they are genuinely random.
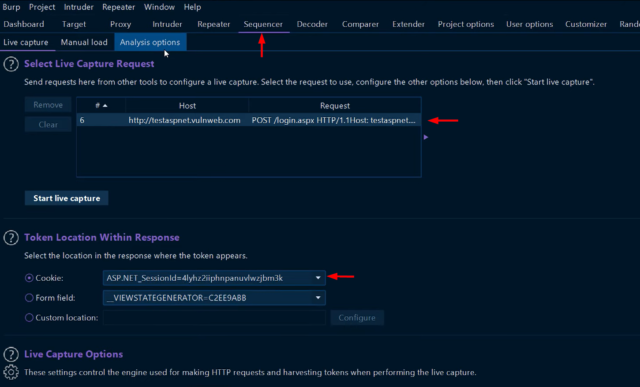 Fig: Sequencer tool tab in BurpSuite
Fig: Sequencer tool tab in BurpSuite
Decoder
In Burp Suite, people use the Decoder tool to decode and encode data in different formats. It provides a simple and efficient way to convert encoded data into a human-readable format, making it an essential tool for testing and debugging web applications. The Decoder tool supports a wide range of encoding formats, including URL encoding, HTML encoding, base64 encoding, and many others. It also supports multiple data formats, such as strings, files, and binary data.
Conclusion
It’s an essential tool for web application testing. With its comprehensive and integrated platform, you can perform various types of security testing, including web application scanning, vulnerability identification, and exploitation. Whether you are a security professional, penetration tester, or web developer, Burp Suite has everything you need to identify and exploit security vulnerabilities in web applications.


Excellent blog Sanskar Dwivedi, a complete one… I guess this has a cost but it worth the benefits.
Thanks to you for sharing with us.
Thank You Jorge Velasquez!!
Thanks for giving us a great article