If you’re a web application testing or security professional, you’ve likely heard of Burp Suite. This powerful tool is widely used for web application testing and is a go-to for many professionals. One of the most useful features of Burp Suite is its spidering functionality, which allows you to quickly and easily map out a website’s structure and identify potential security vulnerabilities. In this blog, we’ll look closer at testing with Burp Suite’s Spider and explore some best practices for using this powerful tool effectively.
Getting Started with Burp Suite’s Spider
Before we dive into testing with Burp Suite’s Spider, let’s take a quick look at what a spider actually is. A spider is a program that automatically crawls through a website, following links and identifying all the pages and resources that make up the site. This is a useful starting point for any web application testing, as it helps you understand the structure and scope of the site you’re testing.
To start with Burp Suite’s Spider, you’ll first need to install and launch the tool. Once you’ve done that, navigate to the “Spider” tab in the top navigation bar. From here, you can configure the spidering options and start the scan.
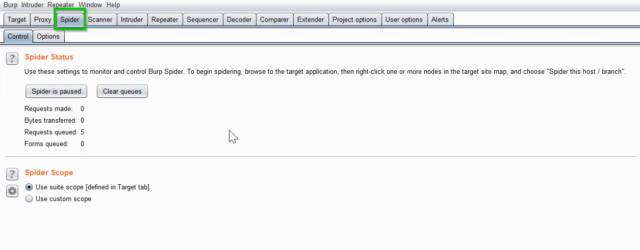
Fig 1: Spider Tab in Burp Suite
Configuring Burp Suite’s Spider
Before you start the spider scan, you’ll need to configure a few options. In the “Spider” tab, several sub-tabs allow you to customize the spider’s behavior. The most important of these are:
- “Scope” – This tab allows you to define the scope of the spider scan. You can specify which pages to include or exclude from the scan and which domains to include or exclude.
- “Options” – This tab allows you to customize the spider’s behavior. You can follow external links, ignore robots.txt directives, and more.
- “Session handling” – This tab allows you to configure the spider to maintain a session with the target site. This can be useful for testing authenticated areas of the site.
Once configured with these options, you can start the spider scan by clicking the “Start” button in the top navigation bar.
Interpreting the Results
Once the spider scan is complete, you’ll be presented with a list of all the pages and resources discovered during the scan. This can be overwhelming at first, but it’s important to take the time to carefully review the results.
One of the most important things to look for is unexpected or unusual behavior. For example, if the spider discovers a page that shouldn’t be publicly accessible, this could be a sign of a security vulnerability. Similarly, if the spider discovers a page that appears vulnerable to SQL injection or another common attack vector, this could cause concern.
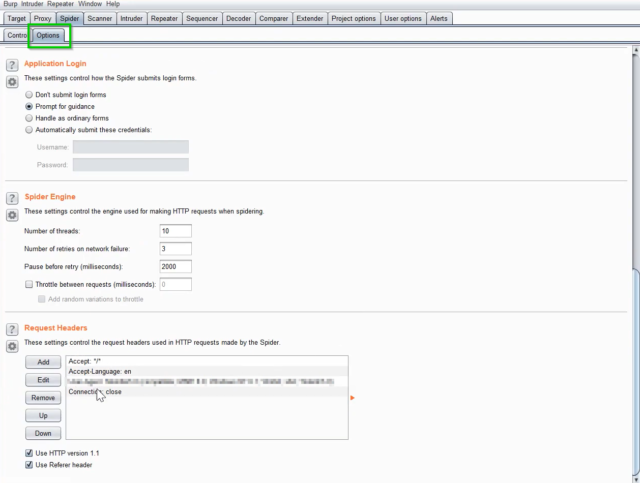
Fig 2: Options tab inside Spider tab in Burp Suite
Best Practices for Testing with Burp Suite’s Spider
- To get the most out of Burp Suite’s Spider, it’s important to follow some best practices. Here are a few tips to keep in mind:
- Take the time to configure the spider scan properly. This will help ensure you get a complete and accurate picture of the target site.
- Be sure to review the results carefully. Don’t just skim through the list of pages and resources – take the time to click through and verify that everything looks as expected.
- Look for unexpected or unusual behavior. This can be a sign of a security vulnerability that you may have missed otherwise.
Don’t rely solely on automated tools. While Burp Suite’s Spider is a powerful tool, it’s important to perform manual testing to ensure you’re catching everything.
Conclusion
Burp Suite’s Spider is a valuable asset for anyone in web application testing. By effectively using this tool, you can gain insights into the structure and scope of the target site and uncover potential security vulnerabilities that may have gone unnoticed otherwise. However, it’s important to remember that automated tools like Burp Suite’s Spider should be complemented by manual testing and expert analysis to ensure comprehensive coverage and accuracy. Overall, by following best practices and carefully reviewing the results, you can make the most out of Burp Suite’s Spider and improve the security of your web applications.