Introducing The Ransomware Survival Guide
Time and time again, we’ve heard these two burning questions from so many organizations: “How do we protect ourselves against ransomware?” and “Where do we start?”
We’ve all seen the ransomware “research” landscape — littered with top-10 lists, vendor cure-alls (spoiler: don’t depend on one security tool to completely eradicate ransomware), and so many other things that confuse, frustrate, and anger security practitioners.
We talk to Forrester clients and security pros every single week about what they can do to have a fighting chance against ransomware and immediately recognized that security pros need help. But we didn’t stop there: We surveyed a broader swath of practitioners to understand how they were defending against ransomware right now and how big of a threat they considered ransomware to be to their organization.
This research led us to recognize a deep void in prescriptive defense recommendations and a concern among practitioners that they were missing “something” that would inevitably allow them to be attacked. So, we spent the last several months working to arm them with a tool that is actionable and descriptive in defending against ransomware. We dove into researching what was critical to organizations to inform what tools and processes they needed to implement, where they needed to implement them, and why they needed them.
The Ransomware Survival Guide is the definitive manual for prescriptive ransomware defense, with over 50 recommendations for what you can do today to stop ransomware. Explore the guide here.
The best part of this tool is that it provides a combination of advice based on what tools and capabilities are available in the environment today as well as what tools security pros can add in the future. This is not just a grocery list of tools to buy — it’s also prioritized configuration changes, process alterations, and, longer term, a path to a Zero Trust strategy.
What Is The Ransomware Survival Guide?
The Ransomware Survival Guide is a toolkit that contains all the things security practitioners and leaders need to implement for a strong ransomware defense strategy. In our research and through our experience, you don’t buy your way into a robust defense. You have configurations, native tooling, and existing tools that can all contribute to reducing your exposure to ransomware and other destructive attacks.
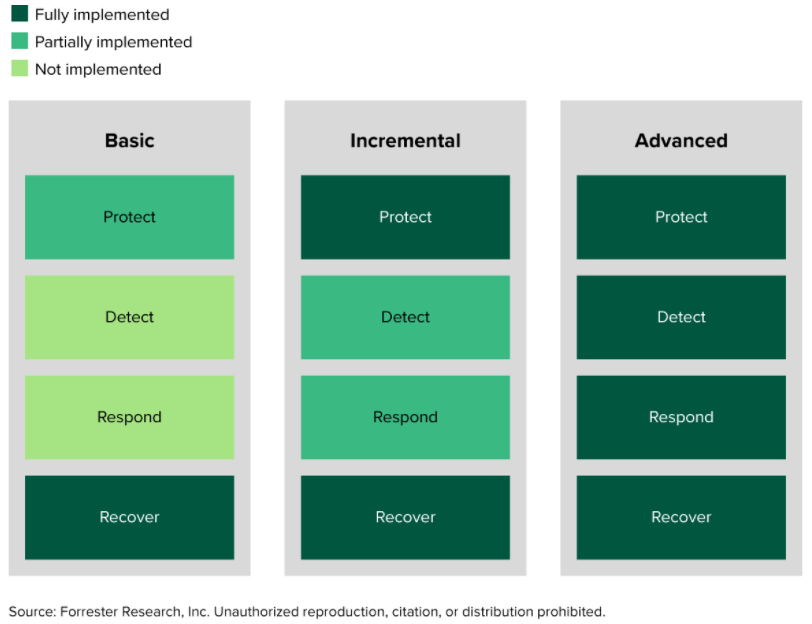
The maturity stages of ransomware defense
As part of the research, we designed maturity stages of ransomware defense, ranging from basic, incremental, and advanced. The research and the tool provide a strategic, 30,000-foot view you can communicate to the board along with the tactical, prescriptive guidance your security team needs.
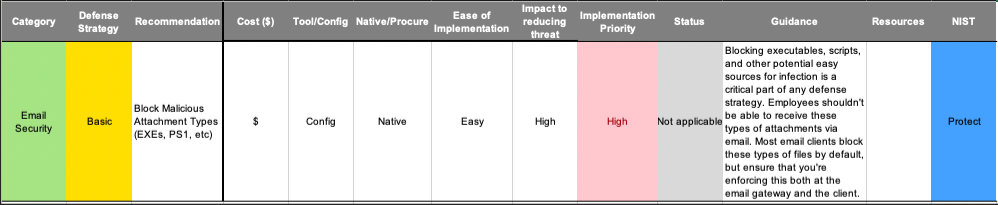
Within the prescriptive guidance, we determine the following factors for every single recommendation: category, cost, whether it is a tool vs. configuration, whether it is natively available or requires procurement, how easy it is to implement, the impact to reducing the threat, a NIST framework mapping, actual in-depth guidance on how to implement a variety of different technical controls and processes, and a suggested priority for each recommendation.
An example entry from “The Ransomware Survival Guide”
Further, this guide not only gives you these recommendations, but since it is built out into an Excel spreadsheet, it allows you and your team to adjust and track your short-, medium-, and long-term ransomware initiatives. You can use this tool from start to finish to understand where you are on your ransomware defense journey and to prioritize what must come next.
Fight Back Against Adversaries Armed With Information That Matters
What we’ve learned more than anything from researching this topic, speaking to security practitioners, and hearing from Forrester clients is that ransomware defense isn’t impossible when you’re armed with the tools and information you need to get the job done. Most organizations have the technology at their fingertips to effectively limit the impact and fend off a multitude of different ransomware types and other destructive attacks.
Forrester clients (and potential clients): Reach out to us to learn how to use the guide or if you have feedback! Have your teams use this research and information to scope and build out your defenses, because isn’t it time that organizations won a cybersecurity battle for once?